Intel reveals four new Microarchitectural vulnerabilities that impact Hyper-Threading
Intel reveals four new Microarchitectural vulnerabilities that impact Hyper-Threading
While a selection of 8th Generation and 9th Generation processors are safe from the exploit, the majority of Intel CPUs from 2011 or later are impacted, affecting millions of consumer PCs and servers.Â
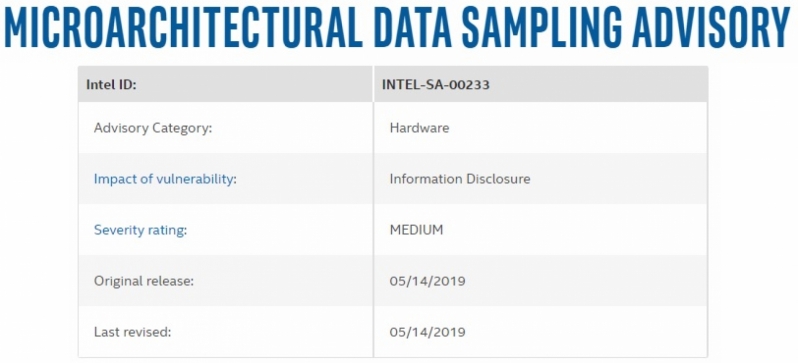
The name of this new collection of exploits is “Microarchitectural Data Sampling” (MDS), with the flaw being discovered by Intel alongside several independent groups. These exploits target Intel’s data buffers, coming with titles such as ZombieLoad, Fallout, RIDL (Rogue In-Flight Data Load) and Store-to-Leak Forwarding.Â
Intel hopes to address these issues with future OS updates and microcode mitigations, though it is worth noting that many of their latest processors already contain hardware level fixes for these issues. Sadly these fixes are likely to come at a performance cost.Â
 Â
  Microarchitectural Data Sampling (MDS) is already addressed at the hardware level in many of our recent 8th and 9th Generation Intel® Coreâ„¢ processors, as well as the 2nd Generation Intel® Xeon® Scalable Processor Family. For other affected products, mitigation is available through microcode updates, coupled with corresponding updates to operating system and hypervisor software that are available starting today.We’ve provided more information on our website and continue to encourage everyone to keep their systems up to date, as it’s one of the best ways to stay protected. We’d like to extend our thanks to the researchers who worked with us and our industry partners for their contributions to the coordinated disclosure of these issues.
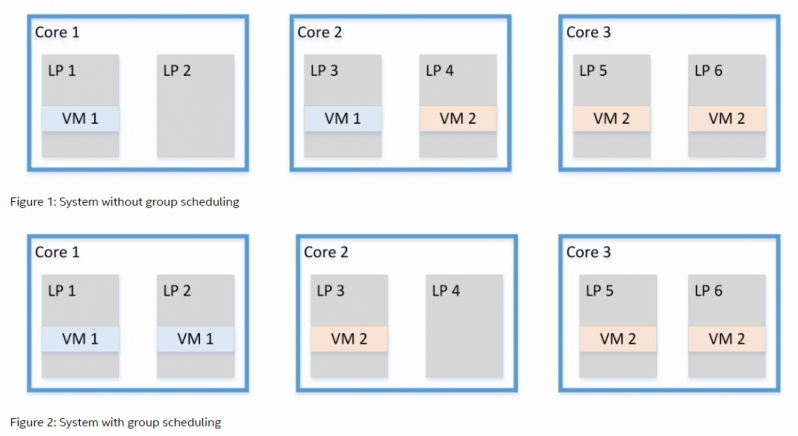
To address these new vulnerabilities, OS makers need to make significant changes to how Hyperthreading functions, giving each thread an extra layer of isolation when programs with different security domains are running. Simply put, these exploits can allow one thread to peak at what the other is doing, and while observable data will, for the most part, be useless it is nonetheless a big concern for cloud systems with multiple VMs or other high-security environments. Â
Intel proposes a solution called Group Scheduling, which will prevent processes from a separate trust domain from running on the same thread. The downside here is that this will undoubtedly prevent full thread utilisation within systems, reducing performance levels. If several programs don’t trust one another it is likely that there will be threads that sit at idle, impacting load balancing and performance.Â
Another solution from Intel is to simply turn off hyperthreading, which will prevent attackers from inferring data through MDS. This is a surefire mitigation for affected systems, but undoubtedly one that will impact system performance. Â
    Â
 Â
Fixing these speculative execution issues isn’t an easy process and there is no doubt that more vulnerabilities will be discovered over the next few years. It will likely take several years for Intel to fully address the risk of Speculative Execution attacks within their processors, and even then there is always the possibility that another exploit is waiting to be discovered.
More information about this new MDS class of vulnerabilities is available on Intel’s website. An in-depth explanation of the issue is available at Red Hat Videos.Â
AMD and ARM processors are unaffected by these MDA-class vulnerabilities.Â
You can join the discussion on Intel’s Microarchitectural Data Sampling vulnerabilities on the OC3D Forums.Â



